Fortifying multi-cloud security: Essential strategies for data security in cloud computing
Ever thought about what makes a castle so secure? Tall walls, watchtowers, guarded gates—each layer strengthens its defense. Just like a fortress, businesses in a multi-cloud world need layered data security in cloud computing to protect their data while maintaining compliance and accessibility. Without a solid strategy, gaps emerge, putting sensitive information at risk.
“It takes 20 years to build a reputation and a few minutes of a cyber incident to ruin it.” — Stéphane Nappo, Vice President, Global Chief Information Security Officer, Group SEB
This quote underscores the critical need for robust multi-cloud data protection. Disjointed protections expose businesses to compliance issues, disruptions, and reputational harm. Without a solid strategy, hidden vulnerabilities can lead to costly breaches. An expert data security service provider ensures a unified approach with tailored security frameworks and proactive threat management. In this blog, we’ll explore strategies to fortify multi-cloud security through a well-orchestrated security ecosystem.
The growing challenge of cloud data security
As cloud usage expands, so do the security concerns—data spread across platforms, inconsistent policies, changing threats, and complicated compliance. A proactive, unified strategy is essential to minimize these risks.
| Challenge | Impact | Solution |
|---|---|---|
| Data sprawl | Hard to track and secure data | Unified security policies |
| Inconsistent policies | Risk of security gaps | Standardized frameworks |
| Evolving threats | Cyberattacks target cloud weaknesses | Proactive monitoring |
| Compliance complexity | Requires continuous enforcement | Automated compliance tools |
| Security vs. access | Hard to balance usability and security | Adaptive access controls |
Key risks of fragmented multi-cloud security
When security isn’t unified, businesses struggle to keep sensitive data safe across multiple cloud platforms. Inconsistent security increases the chances of breaches and complicates compliance. These are the risks organizations need to manage:
-
Data visibility challenges:
Sensitive data spreads across different cloud service providers, making it difficult to track, classify, and protect.
-
Security gaps and misconfigurations:
When policies across cloud platforms aren’t consistent, it creates security gaps that cybercriminals are quick to exploit.
-
Regulatory compliance complexity:
Meeting industry standards (e.g., GDPR, HIPAA) requires continuous monitoring and policy enforcement across multiple platforms.
-
Threat evolution and cloud vulnerabilities:
Ransomware, insider threats, and APTs target security gaps, increasing the risk of data breaches.
-
Balancing security and usability:
Weak access management either restricts productivity or exposes sensitive data to unauthorized users.
-
IAM inconsistencies and lack of centralized visibility:
Managing identities across multiple clouds without a unified IAM approach increases the risk of unauthorized access and privilege escalation.
-
Network security risks and configuration drift:
Unsecured data moving between cloud environments and mismatched security setups can expose vital systems to breaches and compliance failures.
Organizations can reduce these risks with a well-rounded security strategy that centralizes data protection, automates compliance, and keeps threats in check across all cloud environments.
Looking for Azure consulting?
Drive business transformation with our certified Azure consulting. From Microsoft Purview for data governance to secure cloud strategies, we deliver scalable, compliance-focused solutions that maximize value.

Essential features of an effective multi-cloud data security in cloud computing strategy
A strong multi-cloud security strategy ensures data remains secure, compliant, and accessible. Here are the key features:
-
Unified data discovery and protection:
Streamline data discovery and classification to protect sensitive information across cloud platforms while maintaining consistent security policies.
-
Preventing data exfiltration and unauthorized access:
Apply Zero Trust principles with strong access controls, encryption, and data loss prevention (DLP) to keep breaches at bay.
-
Automated data governance and compliance:
Use automated compliance monitoring to meet regulations (GDPR, HIPAA, etc.), reducing manual efforts and risks.
-
Implementing zero trust for cloud data security:
Identity-based access, micro-segmentation, and continuous authentication minimize attack surfaces and strengthen security.
Implementing a robust data protection solution with Microsoft Purview
When paired with expert implementation, Microsoft Purview becomes a powerful enabler of multi-cloud data protection. A seasoned service provider ensures seamless integration, optimizing its capabilities to deliver:
-
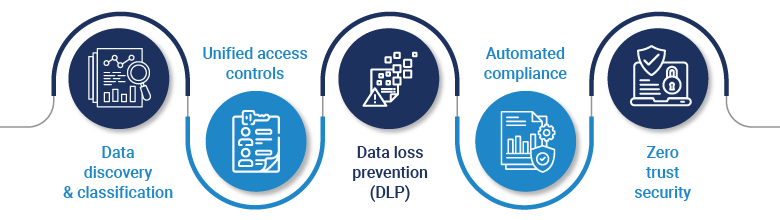
Data discovery and classification:
Identifies and labels sensitive data for proactive security.
-
Unified access controls:
Enforces policies to prevent unauthorized access across cloud platforms.
-
Data loss prevention (DLP):
Monitors data flow and mitigates exfiltration risks.
-
Automated compliance:
Aligns security controls with regulatory requirements.
-
Zero trust security:
Continuously verifies access to reduce credential-based threats.
With the right know-how, businesses can get the most out of Microsoft Purview to boost security, make compliance easier, and remove vulnerabilities in their cloud ecosystem.
“In 2024, mistakes or negligence by business users were the main challenge faced by IT professionals when trying to ensure data security in the cloud, as highlighted by 47 percent of global respondents worldwide.” – Statista
This statistic highlights a crucial reality—technology alone cannot guarantee security. Even the most advanced security tools are ineffective if human errors, misconfigurations, or access control oversights go unchecked. In a multi-cloud environment, these risks multiply due to inconsistent policies and visibility gaps. A structured security approach, combining automation, centralized monitoring, and zero-trust principles, is key to mitigating human-driven vulnerabilities.
Fortifying your cloud security: The path forward
Imagine your multi-cloud security as a castle with layers of defense—moats, gates, and watchtowers. Without a structured approach, vulnerabilities can appear, leaving sensitive data exposed and increasing compliance risks. A unified security strategy, driven by expert solutions, provides smooth protection across all your cloud platforms. From data discovery to automated compliance, the right security framework prevents breaches and enhances resilience. Data security in cloud computing is crucial for businesses looking to safeguard their most valuable asset: information.
Need help securing your cloud environment? Softweb Solutions provides customized solutions powered by tools like Microsoft Purview to protect your data, stay compliant, and tackle risks directly. Contact us now and begin building a robust defense for the future!