DevSecOps stands for development, security and operations. It is a practice that integrates security into every phase of the application or software development lifecycle. It focuses on automating security processes and minimizing vulnerabilities to meet the security and compliance objectives of IT and business. By incorporating security early in the development cycle and integrating it with continuous integration, continuous delivery, and continuous deployment (CI/CD) pipelines, DevSecOps helps organizations ensure the security of their applications.
How to adopt DevSecOps?
These days, culture is the biggest hurdle in adopting DevSecOps, not technology. Historically, security and development teams operated independently. To successfully transition to a DevSecOps approach, both teams need to embrace the DevOps methodology; and application security must be treated as an integrated strategy with a continued focus on security awareness. Here are some effective ways to adopt it:
- Automate the process as much as possible
- Train teams to code securely
- Evaluate existing security measures and identify areas for improvement
- Integrate security into the DevSecOps process
- Use appropriate DevSecOps tools
- Monitor continuous integration and continuous delivery
- Analyze code and perform vulnerability assessments
- Make security a mandatory consideration at every stage
Choose a DevSecOps model that suits the organization’s needs. For example, organizations can opt for
- Software composition analysis (SCA)
- Static analysis security testing (SAST)
- Dynamic analysis security testing (DAST)
- Software composition analysis (SCA)
When you use open-source and third-party components in your code, it’s critical to know how those components are programmed and used so they don’t introduce security vulnerabilities and compliance issues or impact overall code quality. SCA tools can automate this process and provide further insights to identify and mitigate issues. However, you must proactively seek visibility into what third-party components are used in code. Otherwise, it would be difficult to look for issues that SCA tools are designed to mitigate in the first place.
For reference, a similar range of resources known as static application security testing (SAST) tools are designed to identify issues like buffer overflows, cross-site scripting (XSS), and SQL injections. SAST and SCA tools serve different purposes: SAST tools scan your application’s codebase for potential vulnerabilities based on a set of predetermined rules. SCA instead focuses on identifying the open-source codebase so developers can manage their exposure to vulnerabilities and license compliance issues.
Open-source tools:
- OWASP Dependency-Check: OWASP Dependency-Check is a software composition analysis tool that identifies known vulnerabilities in a project’s dependencies.
- Retire.js: Retire.js is a scanner that detects vulnerable JavaScript libraries in your web application.
- WhiteSource Bolt: WhiteSource Bolt is an open-source SCA tool that scans your project dependencies for known vulnerabilities and provides actionable remediation steps.
- Dependency-Track: Dependency-Track is an open-source platform that tracks and monitors your project’s dependencies, providing insights into their known vulnerabilities.
- OSSIndex: OSSIndex is an open-source vulnerability database and analysis platform that integrates with various development tools to provide real-time security intelligence on project dependencies.
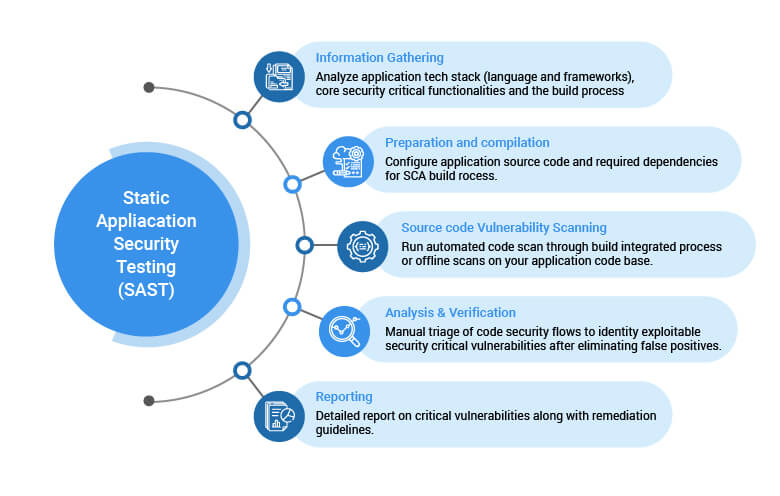
Static application security testing (SAST)
Static application security testing, also known as white-box testing, is a method by which you can test code without running it.
Any developer who has worked with an IDE is familiar with the fundamental concept of static application testing. IDEs often alert developers to potential issues, such as a section of code not being reachable, or a method never being called. Static application security testing is a subset of those tools that focus on security. Some of the most common issues that can be found using SAST are SQL injection vulnerabilities.
SAST tools are high-performance solutions that test code as early as possible and prevent loss of time, work, and possibly fatal security issues down the line.
SAST is an integral part of the shift-left security methodology. Your team will spend less time fixing security issues by checking for potential problems as soon as you type the code. SAST integrates into IDEs and CI/CD pipelines to seamlessly prevent bad code from ever reaching production.
SAST has many benefits. You can integrate these tools into a CI/CD pipeline and alert developers about potential issues early in the development cycle. SAST tools are also very fast, as they do not require compiling or running the code. They simply scan the text for potential concerns and highlight them for developers.
However, those benefits don’t come without potential downsides. SAST tools tend to have a high number of false positives, which can become a nuisance. And when that happens, developers will ignore the warnings. Therefore, it is crucial to have practical SAST tools that avoid a high volume of false positives.
Open-source tools:
- SonarQube: SonarQube is an open-source platform for continuous code quality inspection that includes static code analysis for identifying security vulnerabilities.
- Bandit: Bandit is a Python-focused SAST tool that analyzes Python code for common security issues and vulnerabilities.
- FindBugs: FindBugs is an open-source static analysis tool for Java applications that detects common coding errors, potential vulnerabilities, and performance issues.
- RIPS: RIPS is an open-source PHP security analysis tool that helps identify security vulnerabilities and coding flaws in PHP applications.
- PMD: PMD is an open-source source code analyzer for various programming languages, including Java, JavaScript, and XML, that identifies potential bugs, dead code, and security vulnerabilities.
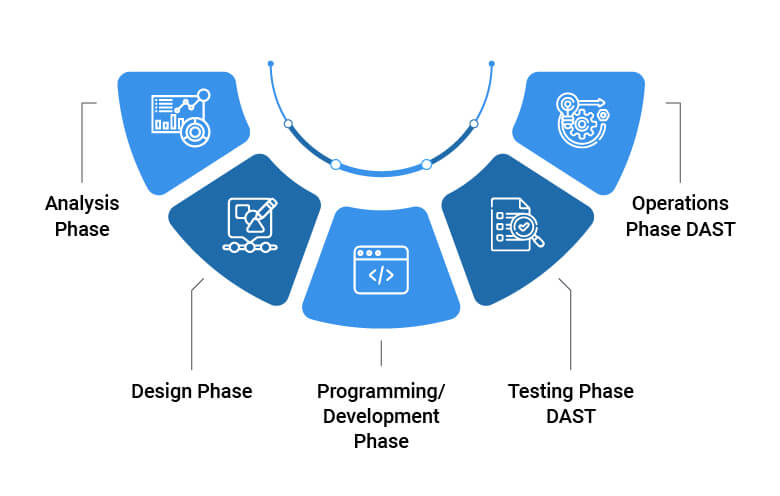
Dynamic application security testing (DAST)
Web application attacks may not get the same headlines that ransomware exploits do, but they are without question a major threat to businesses of all kinds. One of the most common web-based attacks is SQL injection (SQLi), in which an adversary can gain complete control over a company’s web application database by inserting arbitrary SQL code into a database query.
Another is cross-site scripting (XSS), in which attackers inject their own code into a web application with which they may steal user credentials, session cookies, or other sensitive information. Moreover, neither the user nor the company gets any idea about such happening.
Hackers are known to target content management systems and e-commerce platforms because they can harbor a concentration of vulnerabilities that, once discovered, can easily be exploited over and over. Once a web application attack is in progress, the security team may not detect it for quite some time.
DAST tools operate in a similar way, as shown in the figure above. It gives your security and development teams timely visibility into application behaviors and potential weaknesses that could be exploited before an enterprising hacker discovers and capitalizes on them.
Open-source tools:
- OWASP ZAP: OWASP ZAP (Zed Attack Proxy) is an open-source web application security scanner that helps you identify vulnerabilities in web applications.
- Nikto: Nikto is an open-source web server scanner that performs comprehensive tests against web servers to identify potential vulnerabilities.
- Wapiti: Wapiti is an open-source web application vulnerability scanner that audits the security of web applications by performing black-box testing.
- Arachni: Arachni is an open-source, modular web application security scanner that checks for a wide range of vulnerabilities and provides comprehensive reports.
- Grabber: Grabber is an open-source web application scanner that detects security vulnerabilities by crawling and scanning web pages.
Leverage the benefits of the DevSecOps pipeline
Without security, technology-driven livelihoods would be jeopardized; hence, it is critical to implement it early in the software development life cycle (SDLC). Adopting it increases your market credibility and consumer trust.
A DevSecOps pipeline offers the following benefits:
- Earlier detection of security flaws
- Security teams with greater agility and speed
- Programming in a secure manner
- Enhanced speed of recovery in the event of a security incident
Implement SAST using the Azure DevOps Pipeline for .Net Core applications with SonarCloud
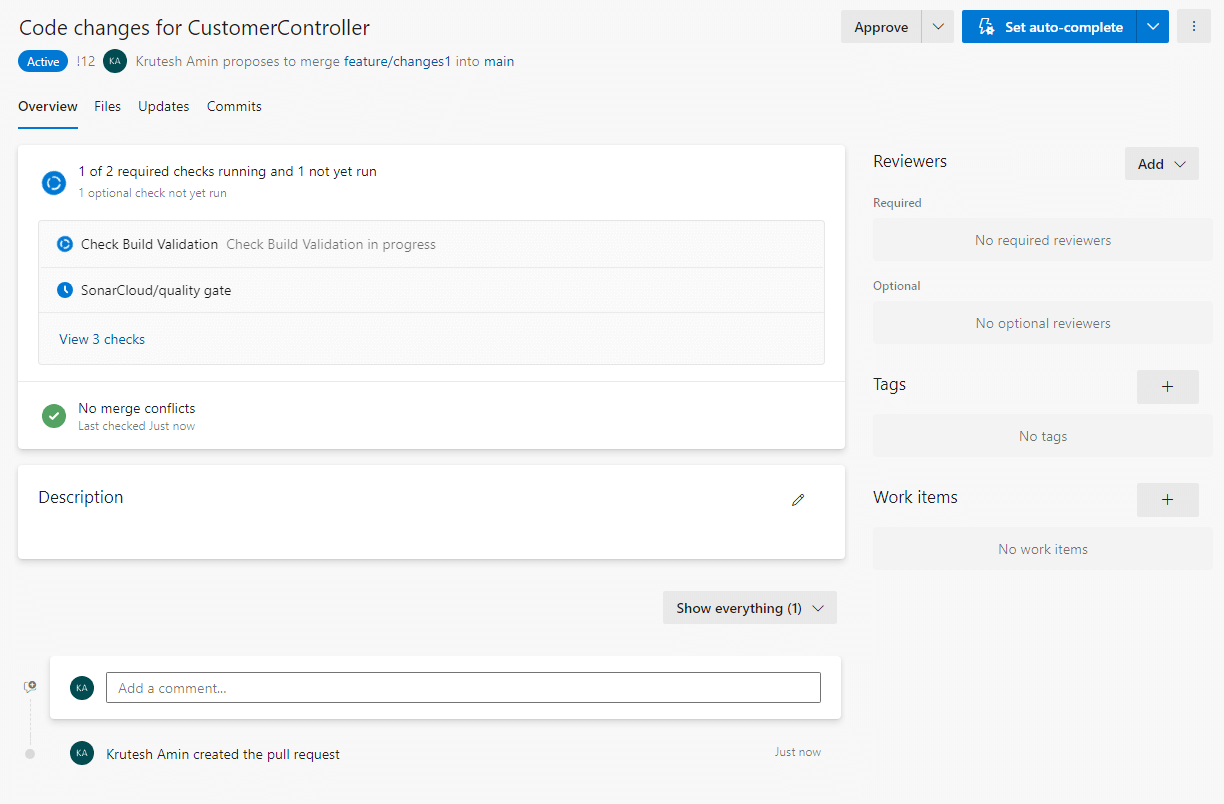
1. Need to install the extension for SonarCloud tool from the marketplace.
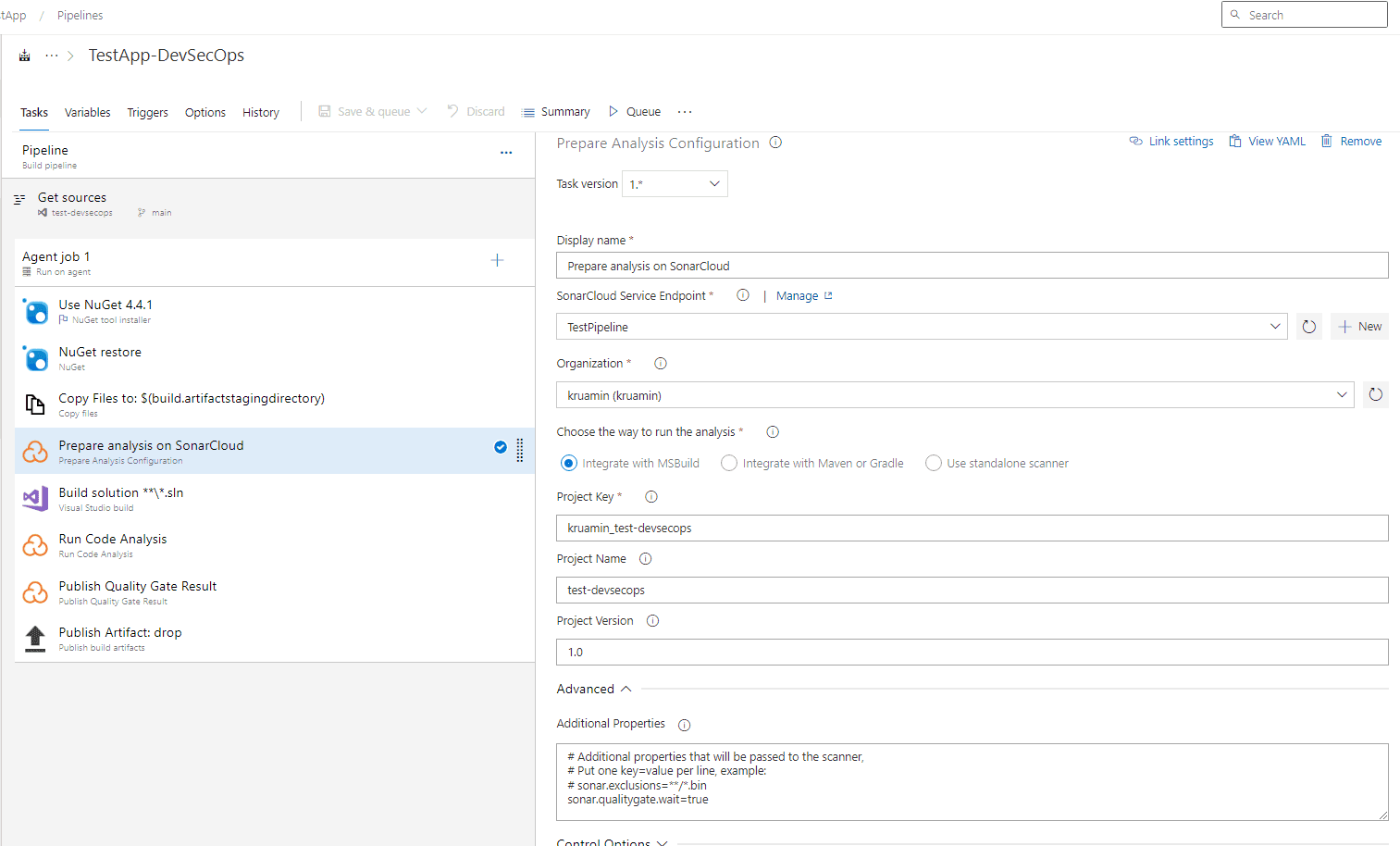
2. Prepare a build pipeline to check and validate the new pull request.
- We primarily need to incorporate three additional steps related to Sonar Cloud. Prepare an analysis on SonarCloud
- Run code analysis
- Publish quality gate results
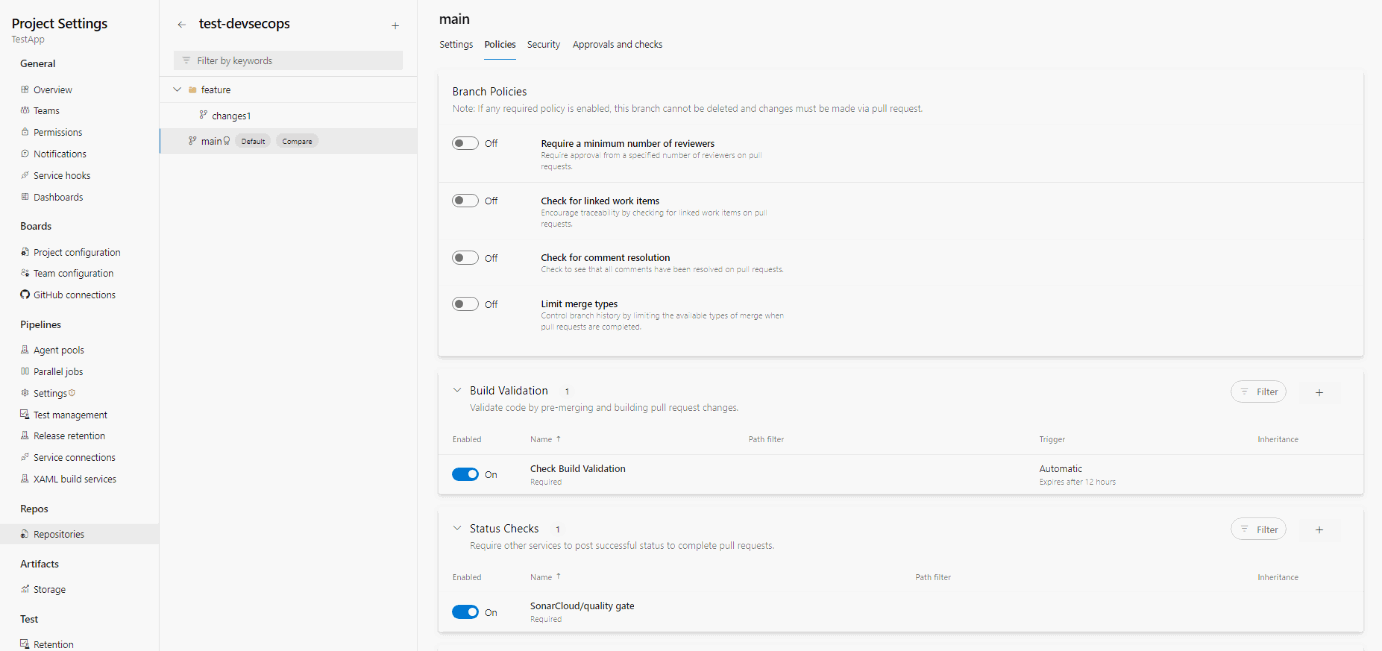
3. We can configure the project settings to validate build validation and quality gate checks.
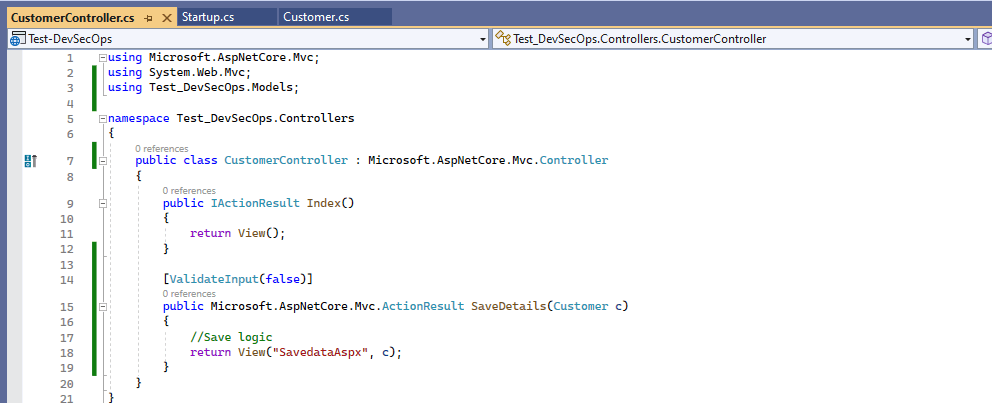
4. Prepared code to address security issues related to XSS.
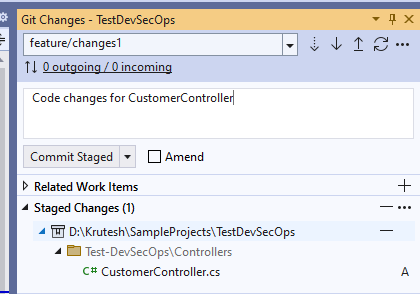
5. Commit and push code to the feature branch.
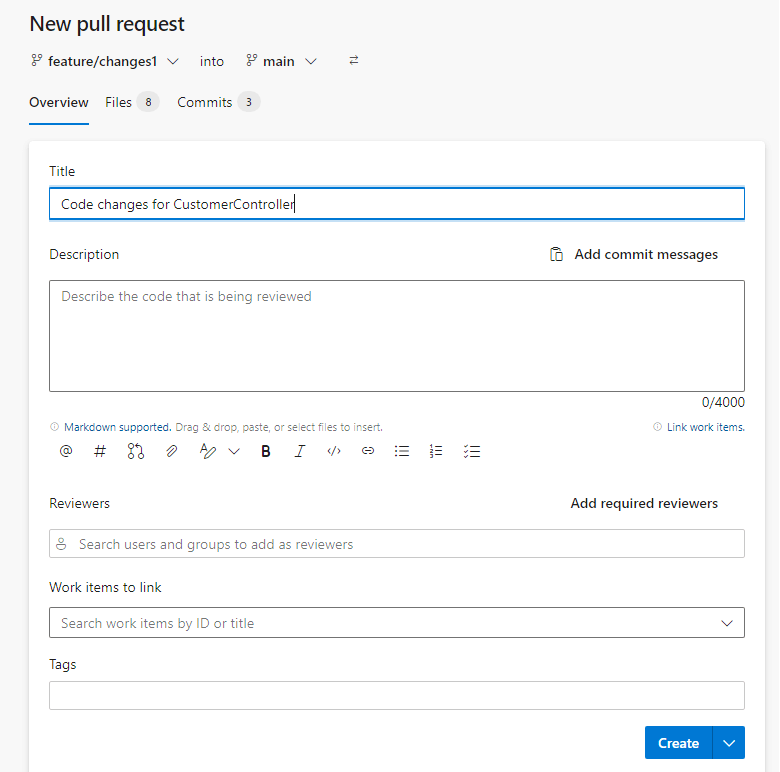
6. Create pull request to merge code with main branch.
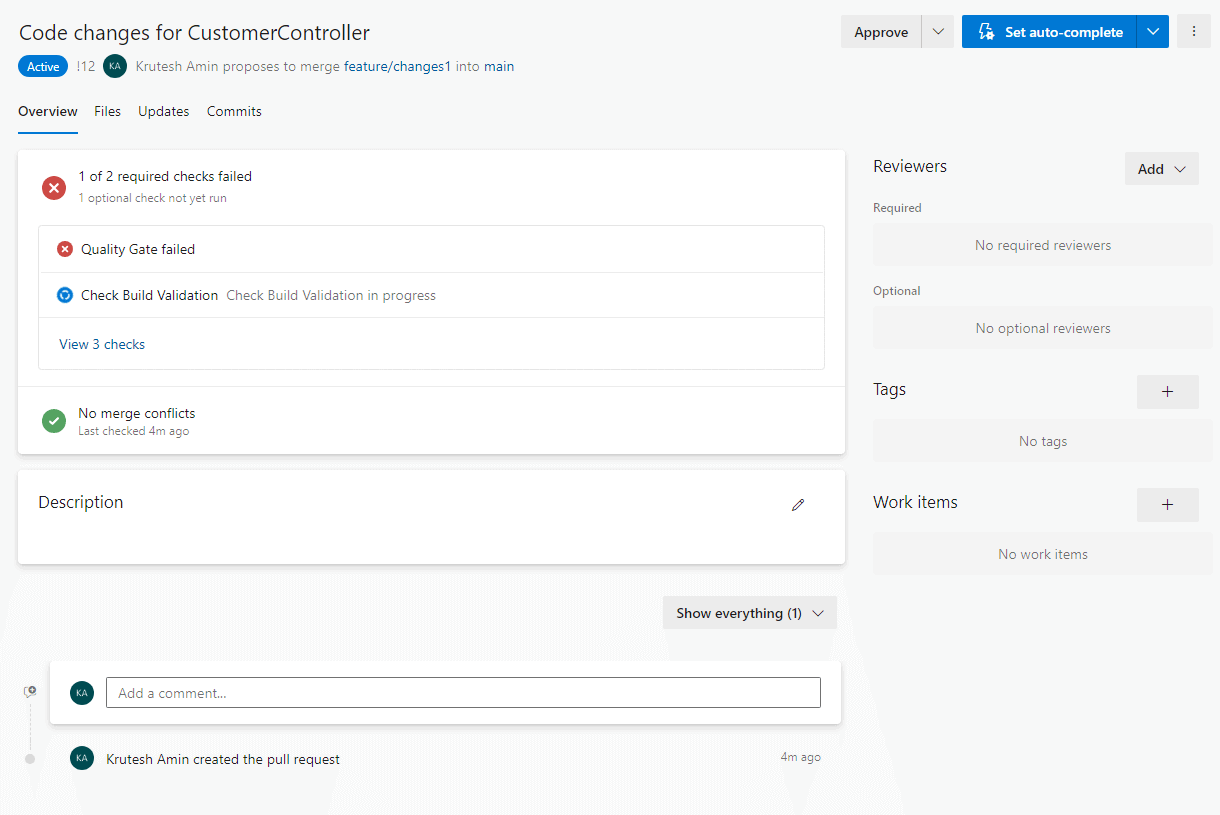
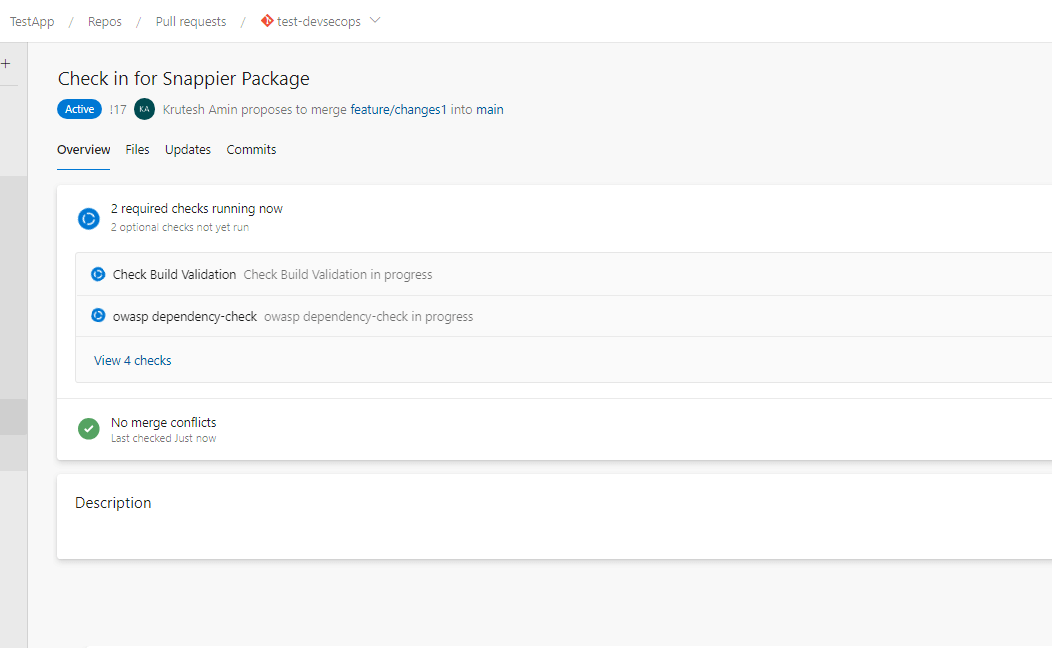
7. After creating a pull request, it will start validating the build and quality gate using the configured pipeline.
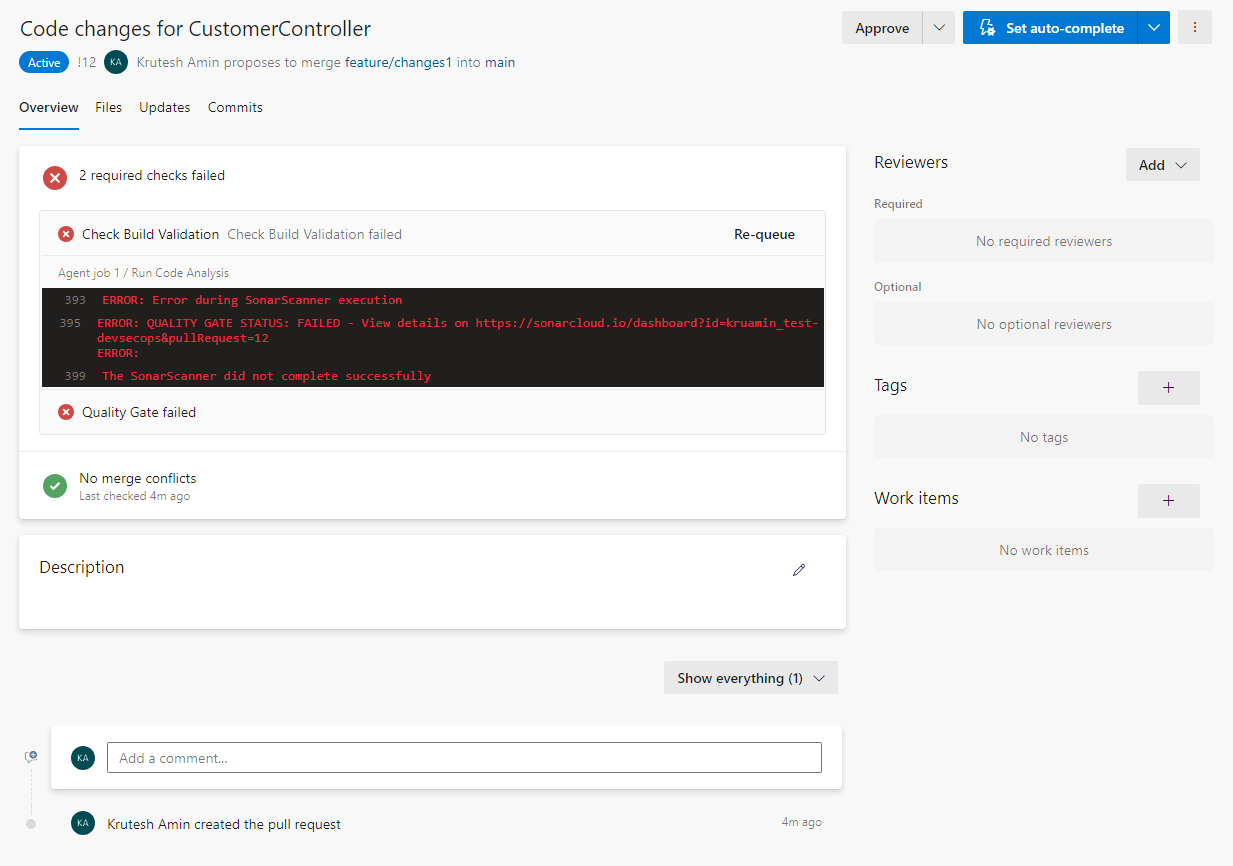
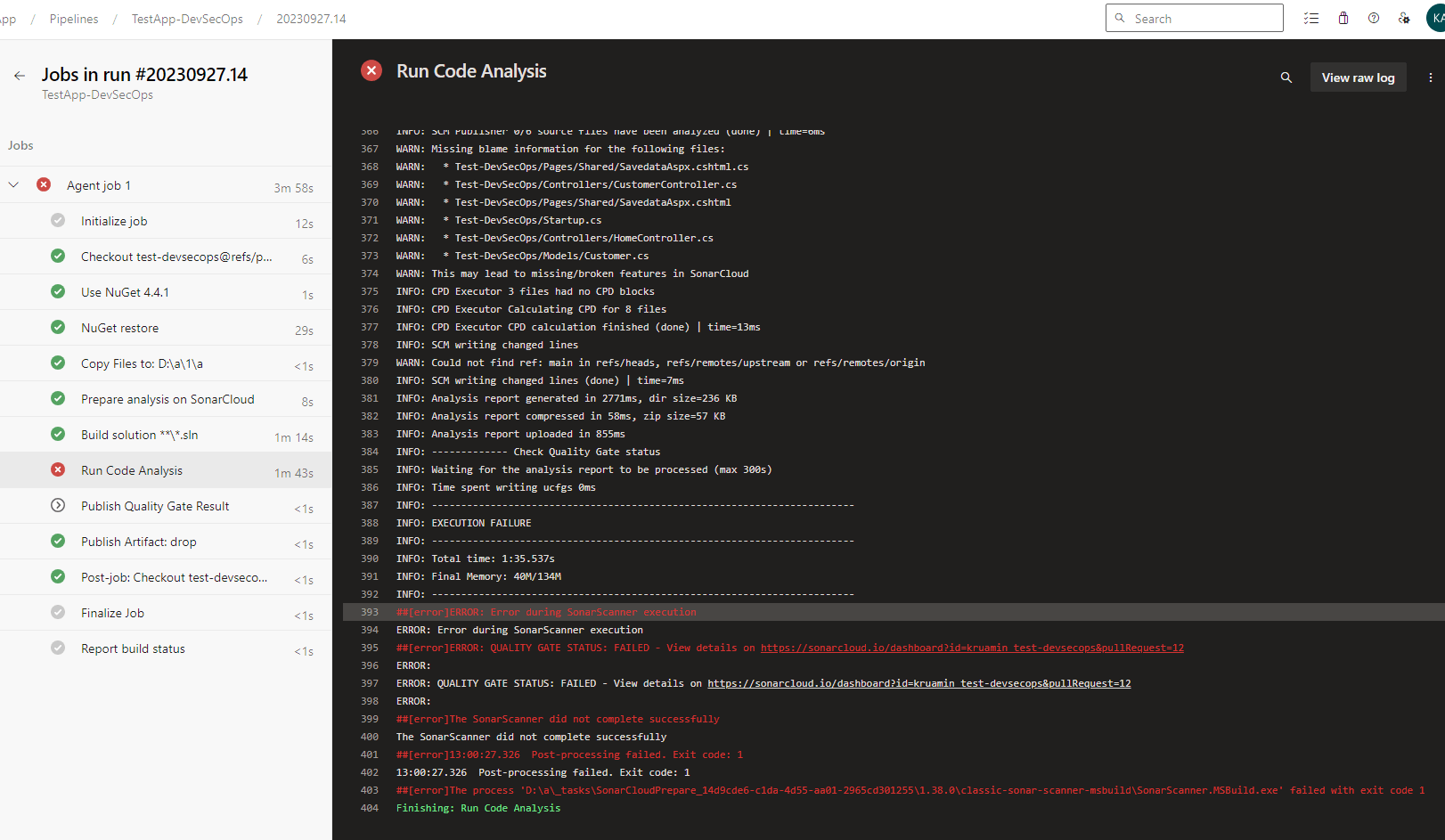
8. We can check the steps of the agent job by clicking on the error summary.
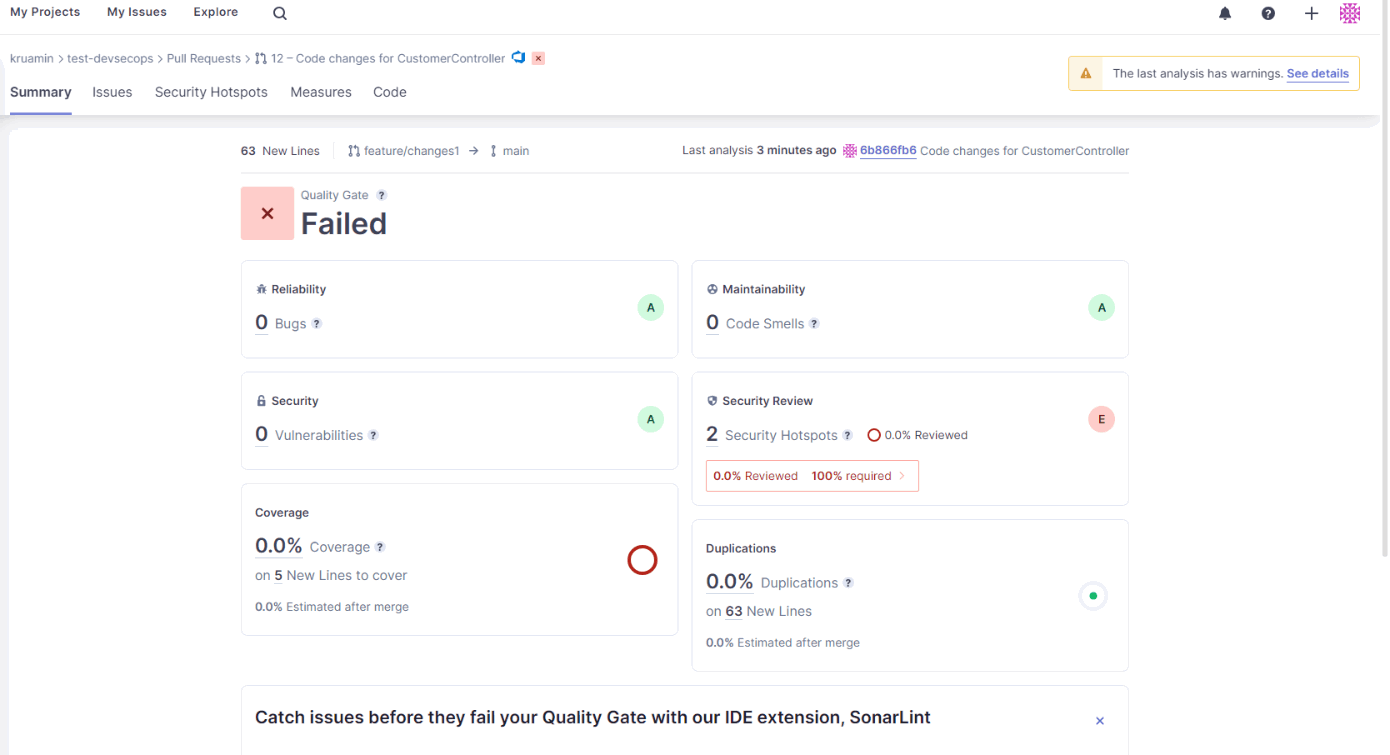
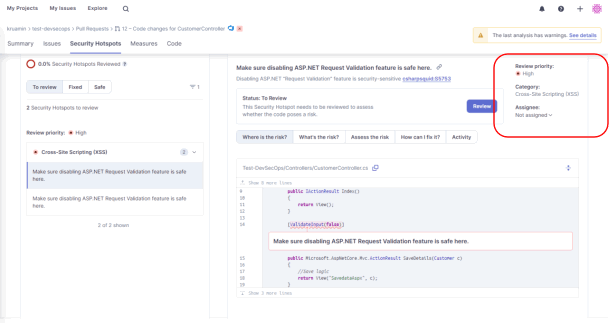
9. We can check the actual code where the error is occurring from the SonarCloud dashboard.
Here, we can see it getting an error related to cross-site scripting (XSS) in the category label on the top right section of the screen.
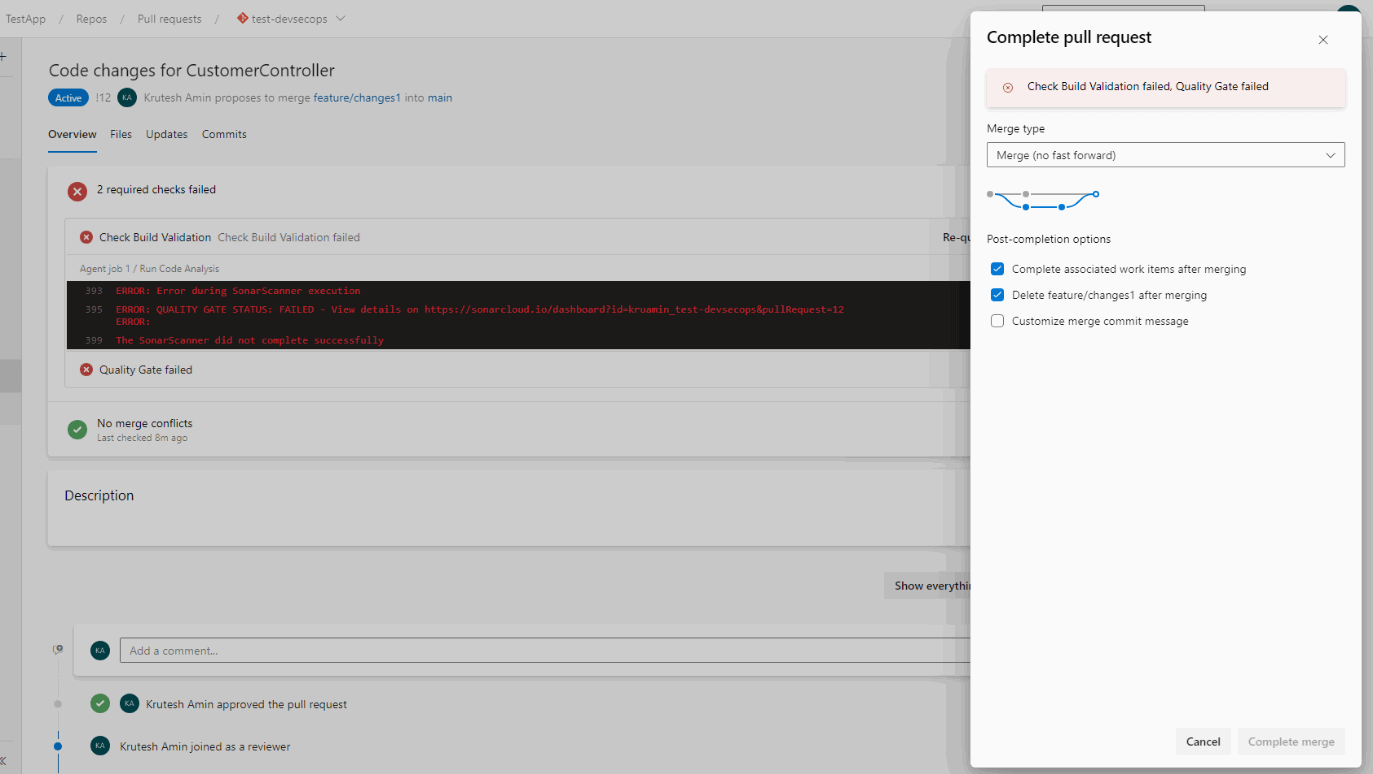
10. It will not allow you to complete or merge a pull request before resolving the issues.
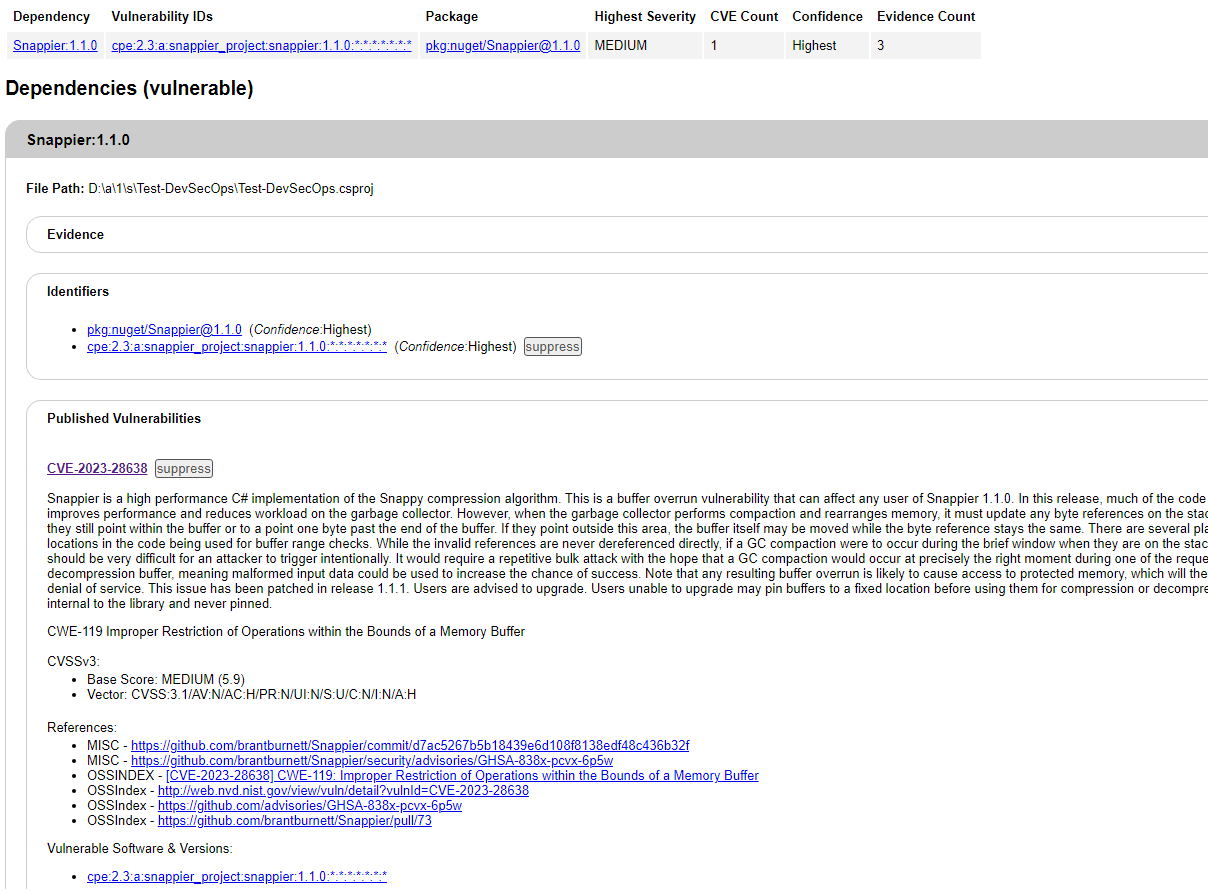
Implement SCA using Azure DevOps pipeline for .Net Core applications with OWASP dependency-check
1. Need to install the extension for the OWASP dependency-check tool from the marketplace.
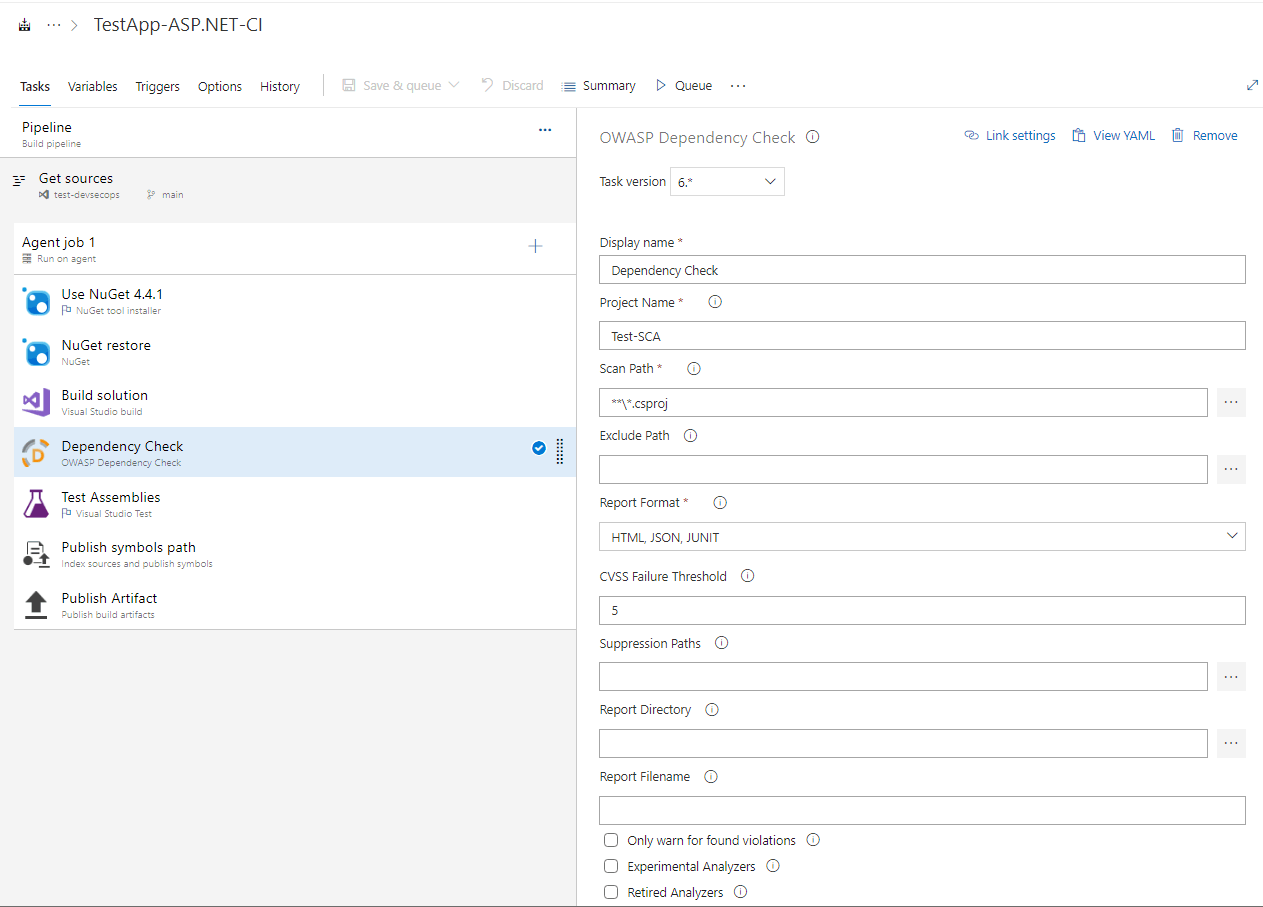
2. Prepare a build pipeline to check and validate the new pull request.
Need to add the dependency check step to the pipeline.
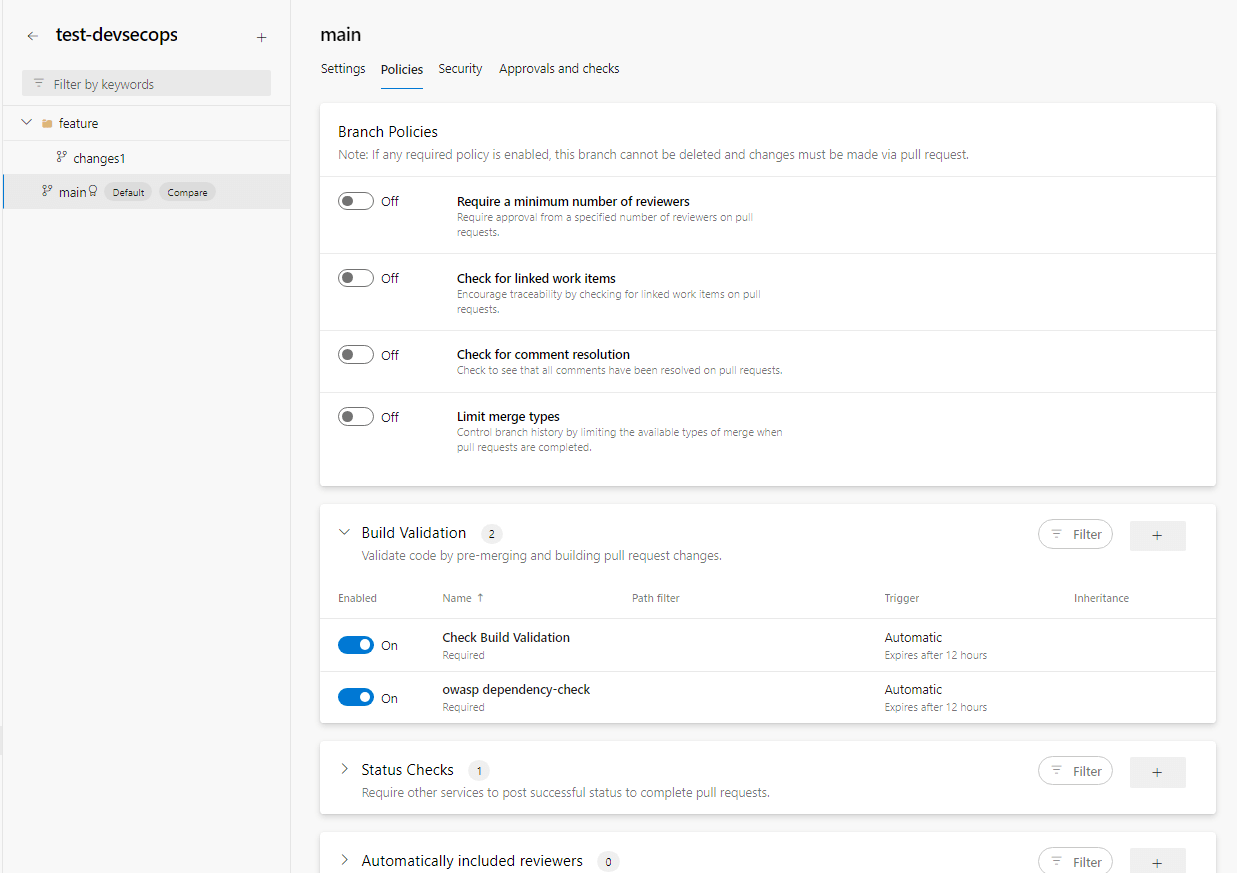
3. We can configure the project settings to validate build validation and quality gate checks.
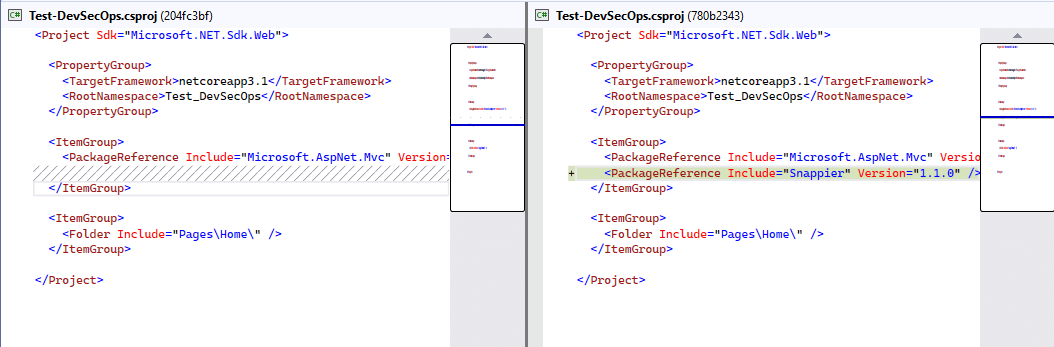
4. Prepared a solution to address security issues. Added a vulnerable package.
5. Commit and push code to feature branch.
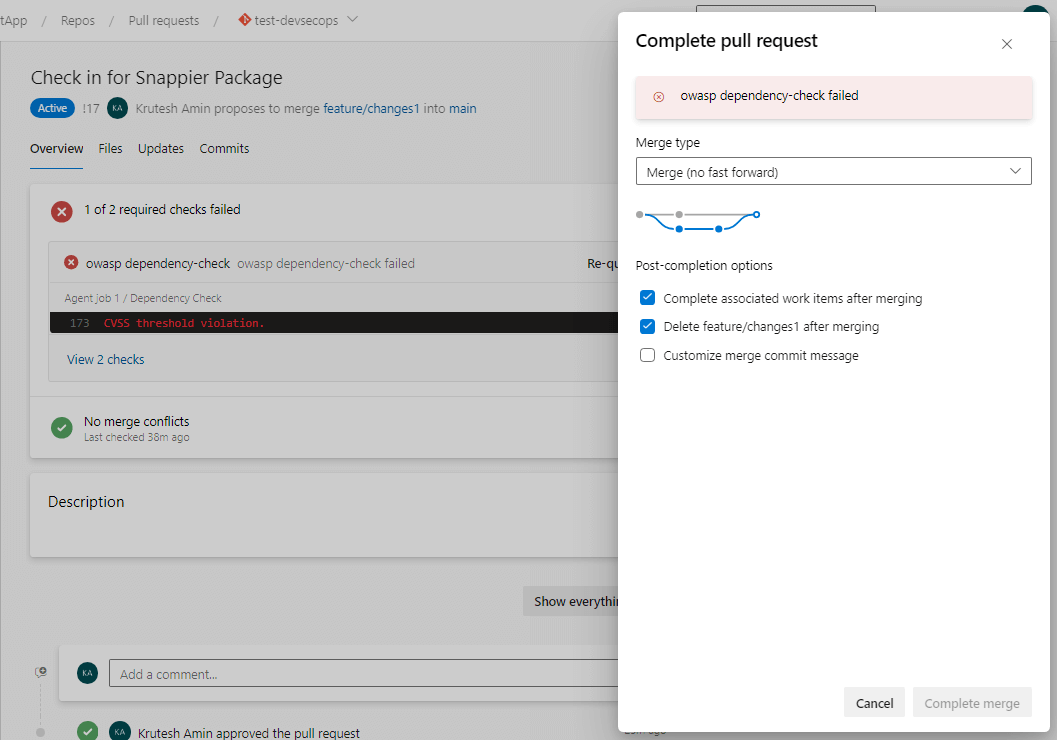
6. Create a pull request to merge code with main branch.
7. After creating a pull request, it will start validating the build and quality gate using the configured pipeline.
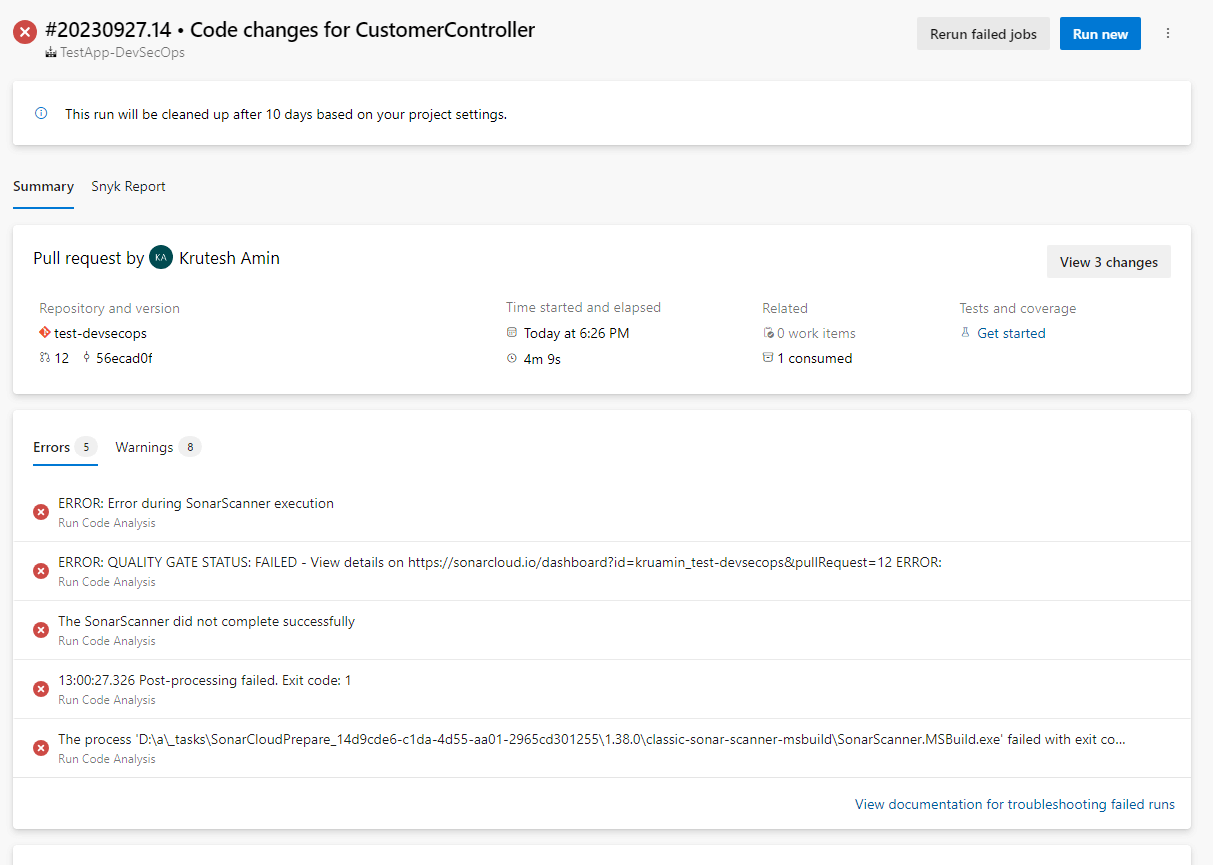
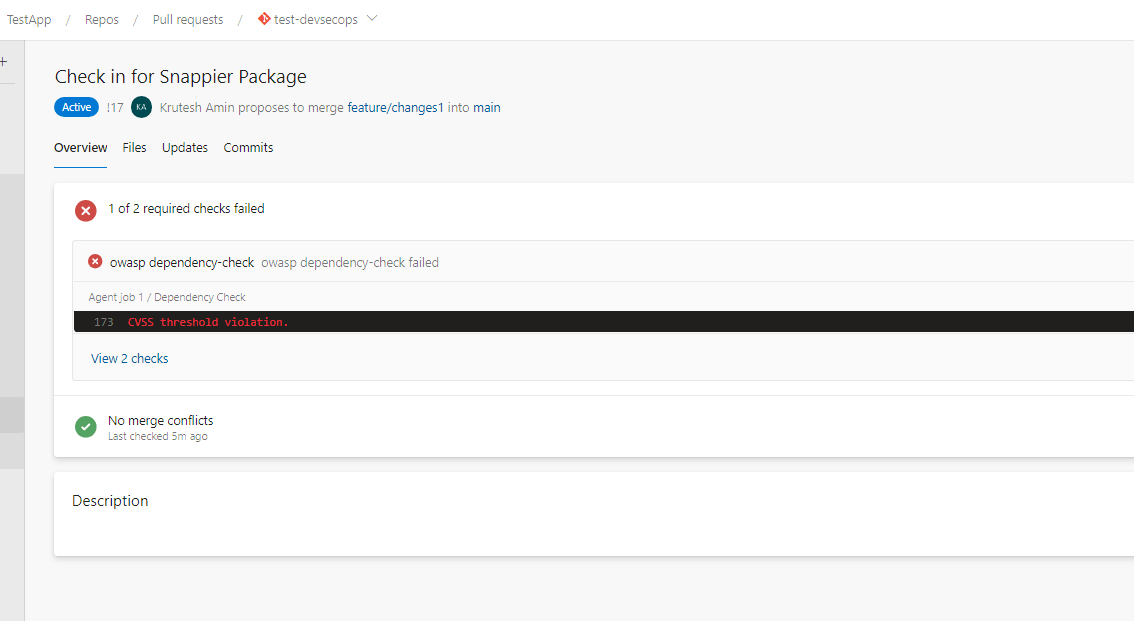
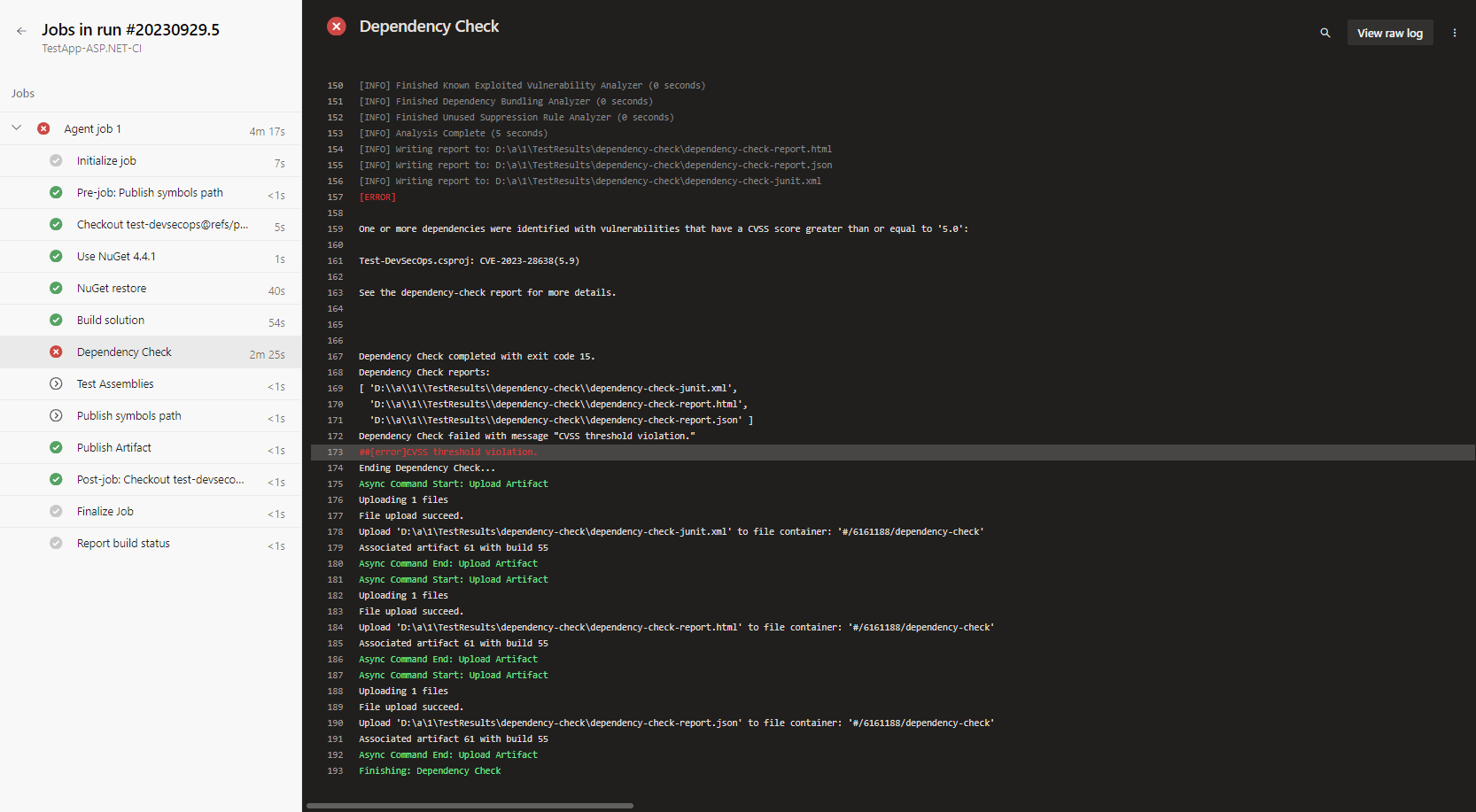
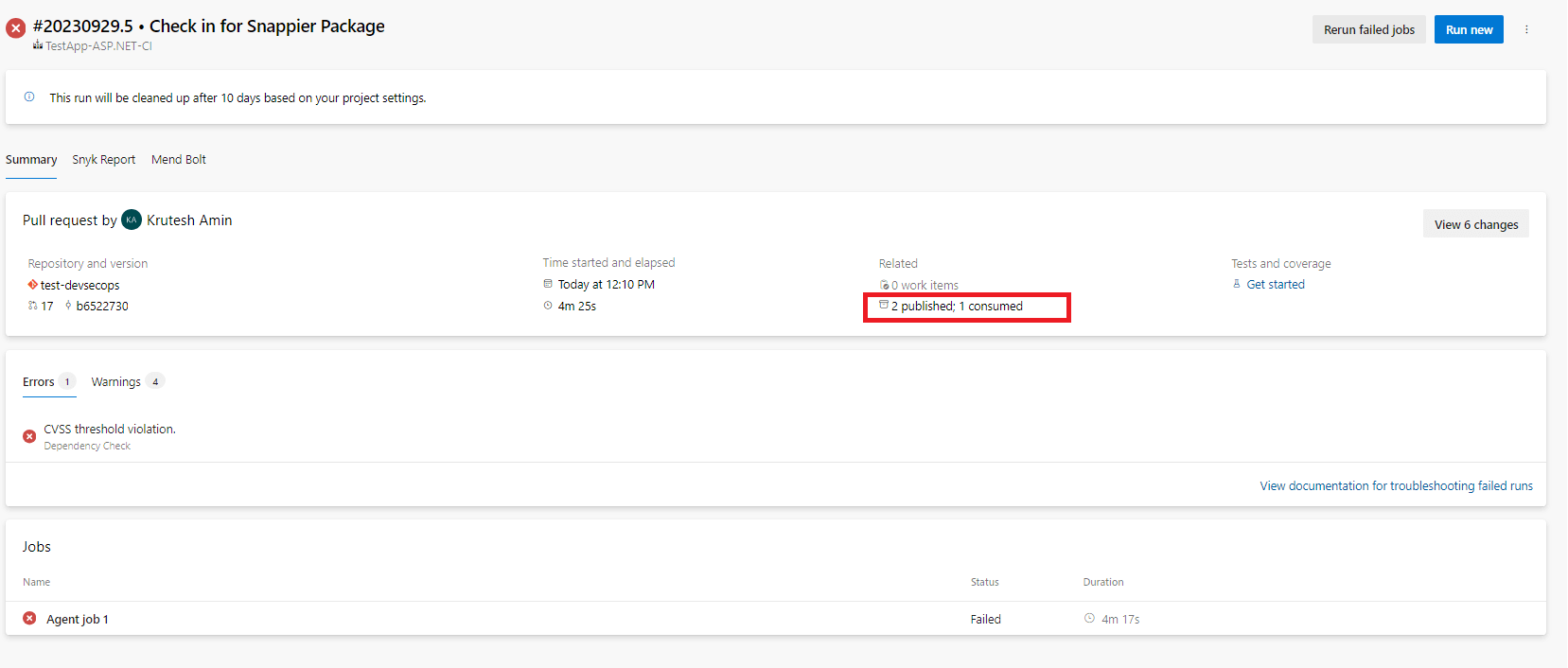
8. We can check the steps of the agent job by clicking on the error summary.
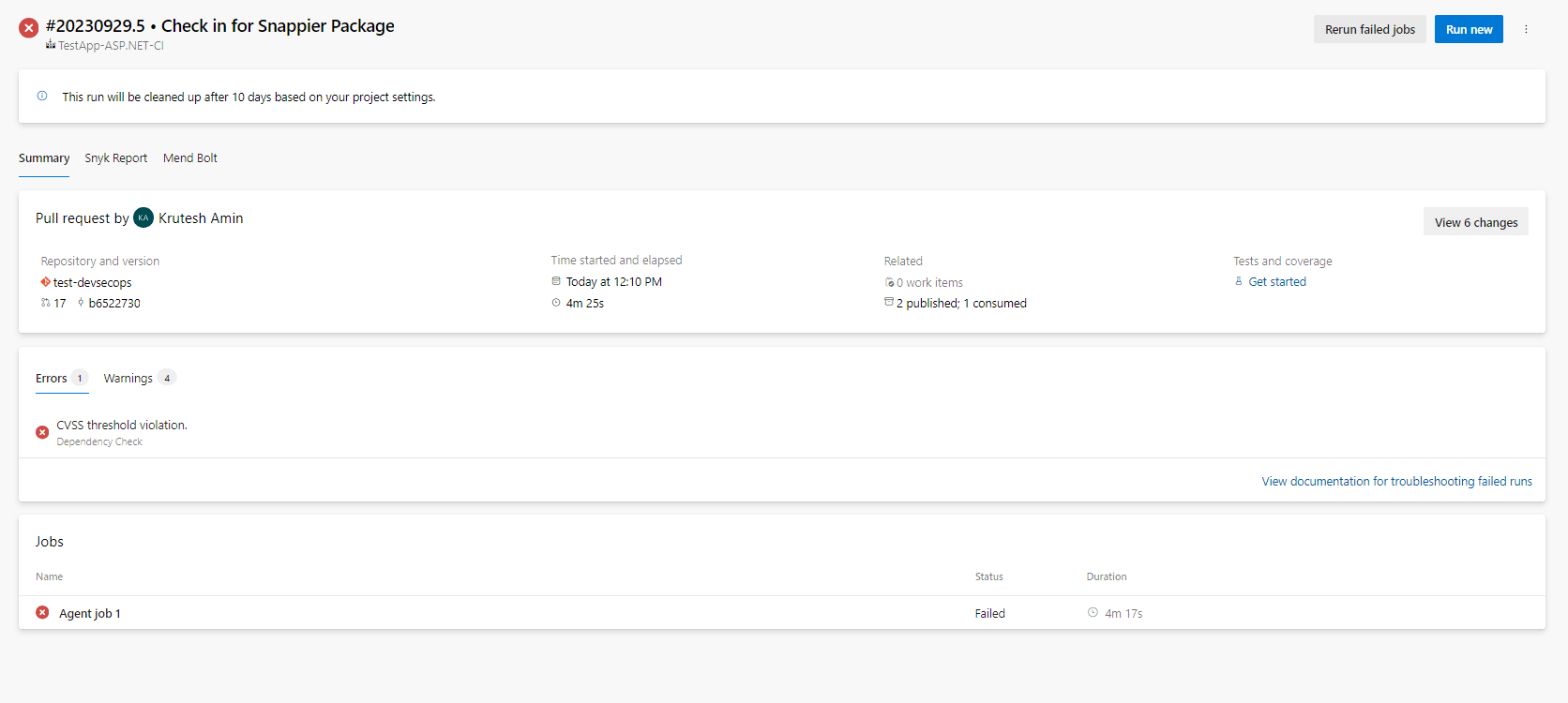
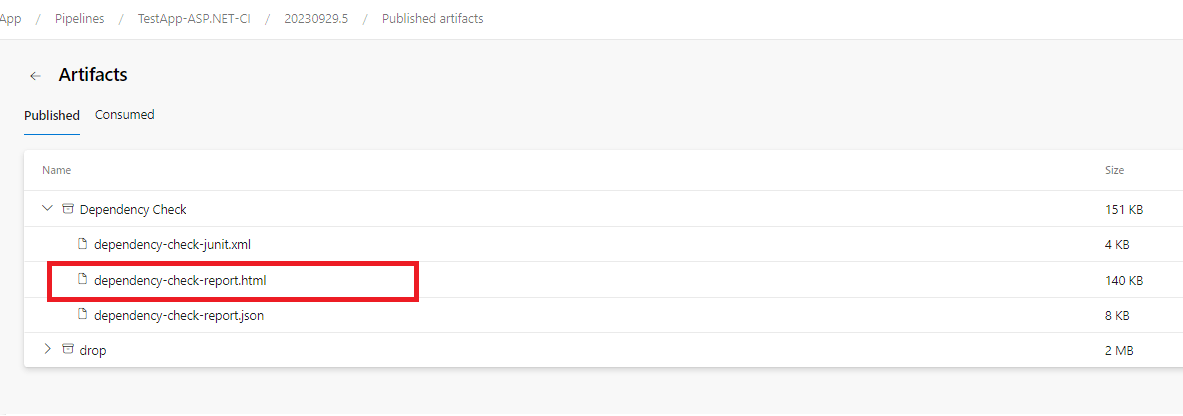
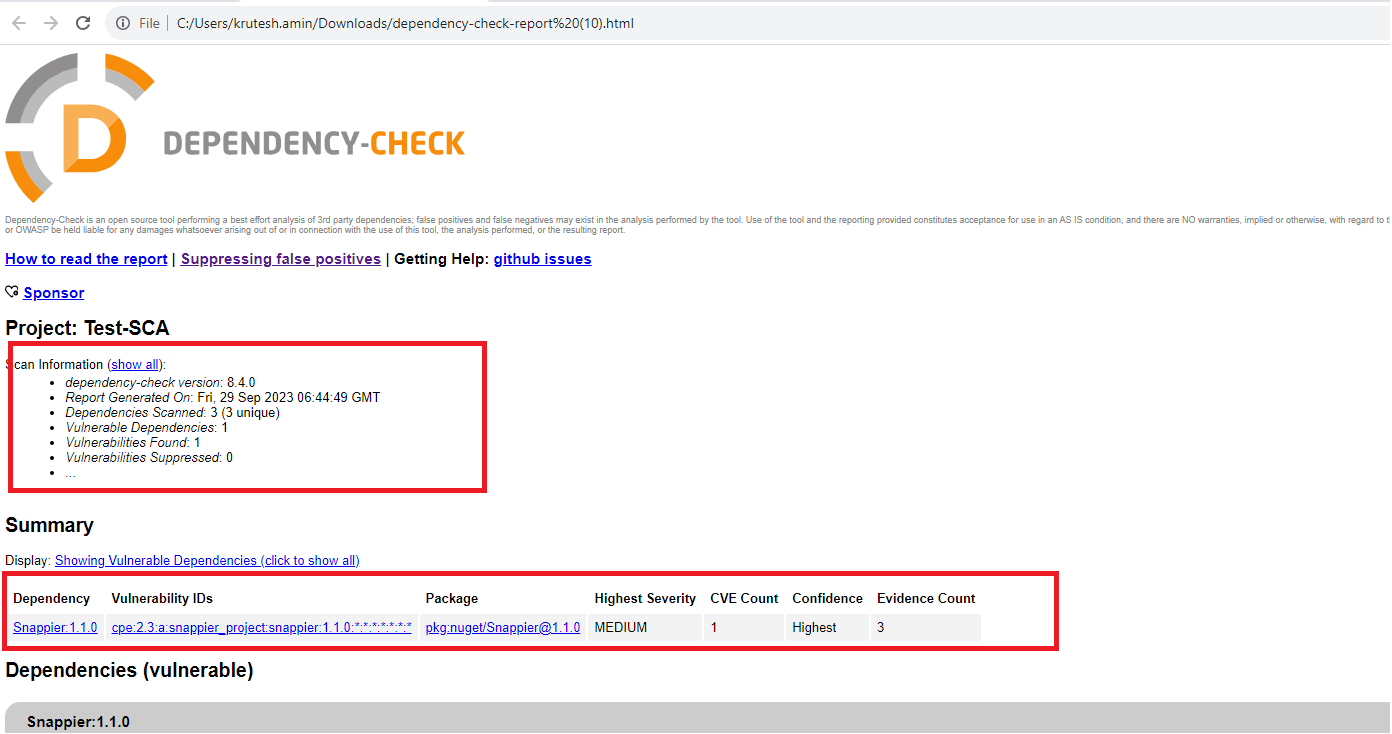
9. We can download and check the actual reports from the artifact.
Here, we can see it getting an error related to vulnerabilities for dependencies.
10. It will not allow you to completely merge pull requests before resolving the issues.
Conclusion
DevSecOps is a crucial approach to ensuring that security is integrated throughout the software development lifecycle. By adopting DevSecOps practices, organizations can build secure and resilient applications while maintaining the agility and speed of DevOps. Leveraging open-source tools, setting up an effective DevSecOps pipeline, and implementing advanced techniques will help organizations stay ahead of security threats and deliver secure software in a rapidly evolving landscape.
Partner with a DevSecOps consulting firm to accelerate your DevSecOps journey and achieve secure and reliable software delivery. With our deep industry knowledge, we can help you implement a DevSecOps approach to maximize your business potential. Contact our DevSecOps engineers today.