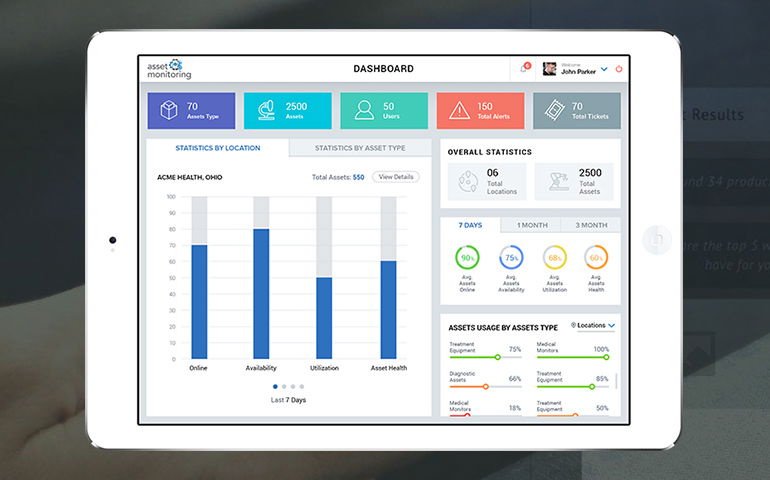
What is the current market scenario for a business and how it relies on assets?
As a business expands, assets have to be purchased, deployed, and maintained in various remote locations. For asset-oriented industries, such as manufacturing, mining, oil & gas, energy & utility, and logistics, regular and constant monitoring of the assets is a mandatory requirement. Moreover, the overall performance of these industries relies upon their assets and any loss or breakdown of the asset can cause some serious damage to the profitability of the company.
The IoT market is expected to reach USD 11 Trillion by 2025, most of which is contributed by insights generated by connected devices in the materials-reliant sector. – McKinsey
A responsive and systematic approach to manage and monitor the asset is a key to maintain the profit quotient of a business. A solution that can collect, analyze, and process the data in real-time to offer meaningful and actionable insights about the assets to business heads and associated stakeholders is something a business truly needs.
However, implementing a smart asset monitoring solution can bring a-bag-full of security and reliability concerns. What are these challenges that must be overcome while implementing an IoT-enabled asset monitoring solution in a company’s business processes?
What are the threats and challenges that affect a business?
Let’s take a walk-through some of the concerns while implementing an IoT-enabled asset monitoring solution.
Theft of data
As it is said, data is the king of any business that wants to flourish today. Every business process is data-oriented. It is the data that helps a company to make decisions that might favor the business. This implies that to have an optimum profit from a business, the data generated by the assets has to be secured. However, the implementation of an IoT-enabled asset monitoring solution brings the risk of data thefts. As the Internet can itself act as a gateway for malicious entities to enter your business eco-system. This as a result leads to loss of confidential business data.
Cyberattacks
The Internet can be a rough workspace. In recent times, we have witnessed various cyberattacks that actually brought businesses to a major halt. A cloud hosted asset monitoring solution is always on the verge of cyberattacks that can completely disrupt the alignment of businesses. For example, cyberattacks can infect the data generated by the asset or alter the location of the asset, making it difficult for the businesses to locate it. Or the assets can be assigned to any irrelevant task making it unavailable for a long period of time.
Relevancy
This may or may not be a security challenge for a smart asset monitoring solution but it’s a reliability issue for business planning to implement an IoT-enabled smart asset monitoring solution. There may be chances that the solution may not work as it is expected to work. It may not monitor the selected asset as it was supposed to, and may deliver incorrect insights.
Integration
A business is an eco-system with a variety of machineries, assets, systems, and people working together. As a result of some technical inefficiencies or human miscalculations, there are possibilities that the asset monitoring solution might not get properly integrated with the existing infrastructure of the company. This might lead to disrupted data generation resulting in the deviation from the desired result.
What strategy should be applied while implementing a smart asset monitoring solution?
In order to maintain the integrity of the implemented asset monitoring solution in the business, one must follow an in-depth defense strategy. Below are the points that cover the steps that a business should follow to overcome the security and reliability challenges while implementing the solution.
IoT-enabled devices
Users must have an authenticated access to the devices connected to the peripherals (assets). Make sure that only authorized users access the assets. This ensures that no unauthorized changes can be made to the assets which can affect the end-result.
Firewall
The firewall of the network that is used to connect the assets with the mainframe must be strong enough to filter the authenticity of users, data, and instructions. Having a strong firewall reduces threats like phishing, trap-doors, worms, viruses and other malicious programs that can hinder or destroy the solution altogether.
User and access management
A company can have multiple users that can use the asset monitoring solution. It is advisable to create a level of authority that allows a pre-defined access to the user based on his authority and designation. This helps an organization to manage the number of users and their relative access to the system ensuring comparatively less human interventions, which results in smooth and hassle-free working of the solution.
Policy compliance
It’s crucial for a company to make sure that the implemented solution is in accordance with policies and standards of the business. Businesses should also ensure the creditability of the solution while working on various proxy servers and compatibility of outbound connections over open ports of the solution.
Benefits
Once the strategy is defined and implemented, it’s time to reap the benefits of the hard work. These are some of the benefits a company can leverage by following a planned strategy to implement an IoT-enabled asset monitoring solution.
Improved responsiveness
A planned strategy allows the solution to work without any unwanted load and data to process. This, as a result, improves the responsiveness of the smart asset monitoring solution.
Reducing the impact of emergencies
The strategy helps the business to prepare for the worst-case scenario with possible countermeasures. This helps the organizations to act effectively during the time of emergency in the business.
Reduce operational costs and improve efficiency
The strategy can remarkably bring down the operational cost of an asset monitoring solution since no additional cost would be required to manage emergencies, breakdown or loss of assets.
Effective asset tracking
The major benefit of applying a defense strategy for a smart asset monitoring solution is that it ensures hassle-free asset monitoring. The strategy allows the businesses to have precise insights from the assets making it easier for them to locate, manage and monitor the assets available at on-sight or in the field.
Conclusion
Softweb Smart Asset Monitoring solution is a perfect blend of hardware, software, and services allowing organizations to have easy tracking and monitoring of the assets. The solution is designed while taking worst-case scenarios into consideration. With pre-planned and well-defined security and reliability compliances, Softweb Smart Asset Monitoring solution can improve asset availability, usage and tracking of assets, resulting in a better business process and profit for the company.